Managed Open XDR
Respond to and neutralize cyber threats in minutes, not days

What Is XDR ?
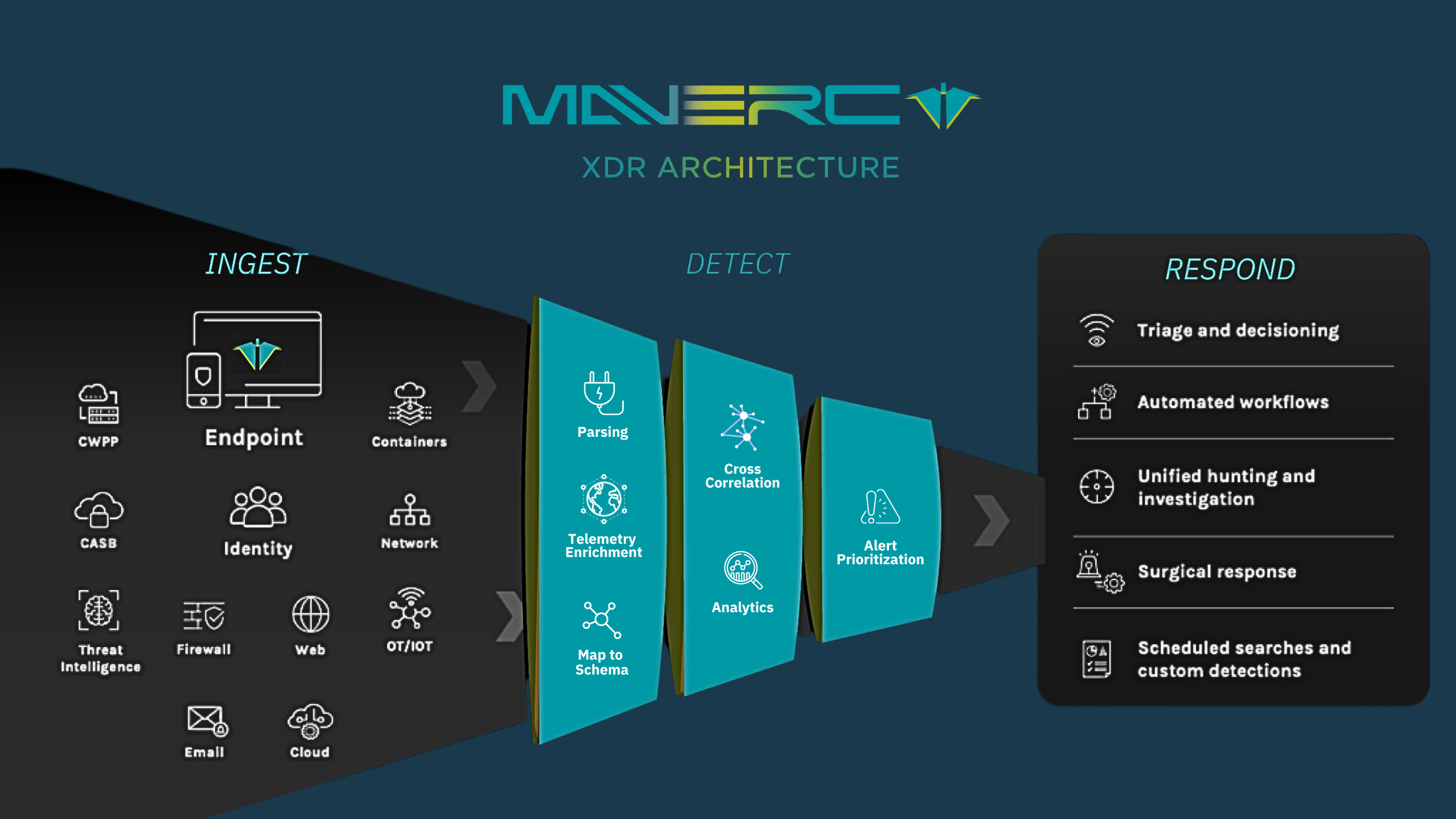
XDR (Extended Detection & Response) represents the next step in threat detection and incident response (TDIR), overcoming the limitations of traditional SecOps platforms by breaking down data and environment silos. This approach enhances visibility across the attack surface, improves threat detection, and accelerates incident response. XDR doesn't render other security controls obsolete; instead, it integrates telemetry from various sources like SIEM, EDR, and UEBA, normalizing and correlating the data to reduce noise, identify true Indicators of Compromise (IoCs), trigger automated responses, and provide actionable alerts.
There are two main types of XDR: Open XDR and Native XDR.
Open XDR, sometimes referred to as Hybrid XDR, is vendor-agnostic and designed to integrate with a wide range of security technologies. This flexibility allows it to ingest data from any source, making it adaptable without requiring the replacement of existing systems. However, it's crucial to assess the quality and breadth of data source integrations that an Open XDR platform offers.
Native XDR, on the other hand, is typically developed by large technology vendors like Palo Alto, Microsoft, or Cisco. These platforms are designed to ingest telemetry primarily from the vendor's own product portfolio, offering a more unified but potentially less flexible approach.
Check Out Our Intro Video

-

XDR
Integrate native telemetry from endpoints, networks, mobile devices, cloud services, intelligence, deceptions, and identity, along with any open or third-party data from your security ecosystem, into a single, powerful platform.
-

MDR
Our open XDR platform covers your entire attack surface with our extensive library of hundreds of data integrations and thousands of threat detections. Get the capabilities of a modern SOC without the cost and headache of managing one.
-

SECOP-AS-A-Service
Be confident in your defenses World-class Threat Hunters and SOC Analysts are devoted to defending you and shutting down threats aimed to harm your business.
We stay ahead of the innovation curve, so you can stay ahead of the threat curve.

Reclaim The Advantage
Our Powerful Platform ingests network, cloud, log, endpoint, and identity signals, correlating indicators of compromise to detect, respond to, and automatically disrupt threats in minutes — with a Mean Time to Contain of 15 minutes.
-
Keeps your network secure anytime, anywhere, 24/7.
-
Fast containment and remediation completed in under 30 minutes, avoiding the cost and hassle of reimaging.
-
Rely on our forensics and IR experts to stop breaches and Identify the root cause of threats to prevent future incidents.
-
Detect threats missed by existing security controls, and turn previously siloed data into high-fidelity, cross-domain attack indicators, insights and alerts to surface the most sophisticated threats

Protect Your Entire Attack Surface
Our open XDR platform provides comprehensive visibility across your entire attack surface, seamlessly ingesting, normalizing, and correlating security telemetry from thousands of data sources. By integrating with your existing tools, it enhances the ROI of your technology stack across endpoints, networks, servers, cloud environments, and SaaS applications.
Why Customers Choose Maverc!
“Were extremely satisfied with the Maverc XDR package. It enables us to concentrate on initiatives that propel our business forward from a security standpoint, with the confidence that Maverc is handling our security needs”

The nature of threats and approaches used by adversaries have changed radically, but the solutions used by enterprises have not. Stop fixating on the perimeter and start looking at your network more like an obstacle course where hackers could be deceived, worn down, paralyzed and ultimately stopped. You protect what matters; they go away empty handed. This is about changing the economics of hacking. Make the cost of the hack impossible for the hackers to justify and you win. Shift your security mindset from “incident response” to “continuous response.” You start by assuming systems are already compromised and require continuous monitoring and remediation.

CyberSecurity designed to protect organizations of all Sizes