Unveiling GrimResource: The Latest Microsoft Management Console Exploit for Initial Access and Evasion
Introduction
The ever-evolving landscape of cybersecurity threats continuously pushes the boundaries of traditional defense mechanisms. The latest addition to this arsenal is the GrimResource technique, an innovative exploit leveraging Microsoft Management Console (MMC) files. This method exploits Microsoft Management Console (MMC) files to gain arbitrary code execution, presenting a significant threat to network security.
What is GrimResource?
After Microsoft disabled macros by default in Office files, attackers began exploring alternative infection vectors. Among the new methods, the use of MSC (Microsoft Saved Console) files has emerged as a potent tool for malicious actors. GrimResource leverages a known cross-site scripting (XSS) vulnerability in the apds.dll library, allowing attackers to execute arbitrary JavaScript within the MMC context.
How GrimResource Works
Exploiting the XSS Vulnerability
The GrimResource attack begins with a malicious MSC file referencing a vulnerable APDS resource in its StringTable section. When the MSC file is opened in MMC, the XSS flaw in apds.dll is triggered, executing arbitrary JavaScript code.
Combining with DotNetToJScript
The attack is further enhanced by integrating DotNetToJScript, which allows the execution of .NET code through the JavaScript engine. This technique is particularly effective in bypassing traditional security measures and delivering payloads like PASTALOADER and Cobalt Strike.
GrimResource Attack Chain
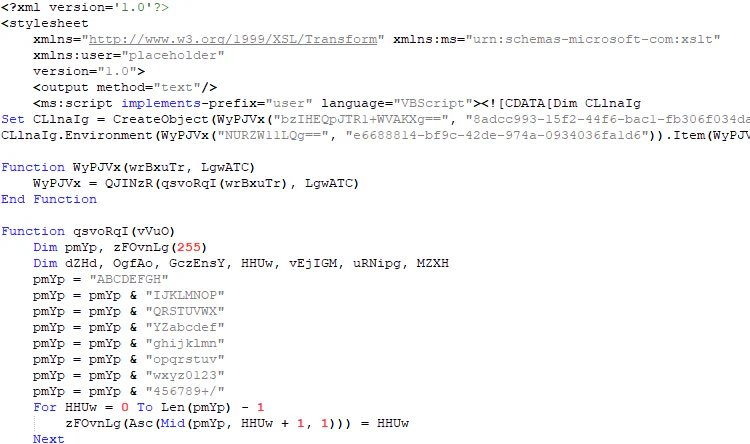
TransformNode Obfuscation: The attack initiates with the transformNode obfuscation technique to evade ActiveX security warnings.
Embedded VBScript: The obfuscated script sets the target payload in environment variables.
DotNetToJScript Execution: The VBScript employs the DotNetToJScript technique to run an embedded .NET loader named PASTALOADER.
Payload Retrieval and Injection: PASTALOADER retrieves the final payload from the environment variables and injects it into a new instance of dllhost.exe using the DirtyCLR technique. In the observed cases, the payload is often Cobalt Strike, a powerful post-exploitation tool.
Detailed Attack Chain
Initial Access
The attack begins when a user opens the crafted MSC file, which then exploits the XSS vulnerability in apds.dll to execute JavaScript code.
Payload Delivery
The obfuscated VBScript reconstructs a VBScript using DotNetToJScript to load PASTALOADER. This loader retrieves the final payload, typically Cobalt Strike, from environment variables and injects it into a dllhost.exe instance.
Post-Exploitation
Once the payload is injected, attackers can execute arbitrary commands, establish persistent access, and exfiltrate sensitive data.
Notable Incidents
The GrimResource technique has been observed in the wild, with samples like "sccm-updater.msc" being uploaded to VirusTotal. Notably, no antivirus engines flagged these samples as malicious, highlighting the effectiveness of this evasion technique.
Detection and Mitigation
Suspicious execution patterns involving mmc.exe and apds.dll.
Unusual .NET COM object creation within non-standard script interpreters like JScript or VBScript.
Temporary HTML files created in the INetCache folder as a result of APDS XSS redirection.
Security Best Practices
Regularly update and patch all software to mitigate known vulnerabilities.
Implement robust security policies to restrict the execution of untrusted MSC files.
Employ advanced threat detection solutions to monitor for behavioral indicators associated with GrimResource.